This Security Policy Management is the cornerstone for your organization’s centralized security, compliance, and asset management, as well as risk assessment.
Security Officers harness the app to author, meticulously review, and seamlessly publish cybersecurity policies, fortifying the organization with comprehensive security risk measures.
Compliance Officers diligently monitor policy adherence and swiftly address violations, ensuring strict compliance with ever-evolving regulations and standards. Disciplinary action can also be tracked for any employee violations.
As guardians of security settings, IT Departments and administrators tirelessly work to maintain an impenetrable digital fortress, guaranteeing a safe and secure operational environment. They employ the latest security protocols, continuously monitor for emerging threats, and share incident response plans – fortifying your organization’s defenses.
Auditors, armed with robust audit trails, conduct assessments with precision and insight, ensuring your organization’s security posture remains resilient. Their thorough examinations not only identify vulnerabilities but also provide valuable recommendations to bolster your security strategy.
Employees, as active participants, engage with policies tailored to their roles, cultivating a united front in creating a cohesive and secure workplace culture. Their commitment to information security policies fosters a sense of collective responsibility and strengthens the organization’s overall security posture against phishing, malware, and all other information security incidents.
Together, This Security Policy Management harmonizes these roles, creating a robust and unified framework that empowers your organization to thrive in an ever-evolving security landscape.
Explore the following resources to help you build your custom Security Policy Management app:
- Emails & Notifications
- Users & Access
- How to Show Records Connected to the Logged-In User
- Workflow & Automation
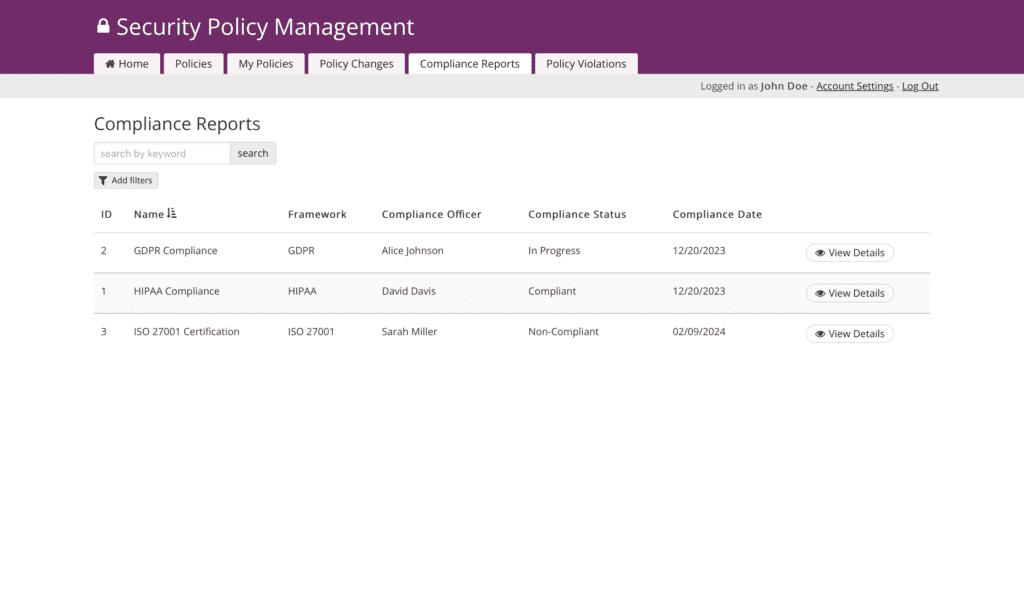
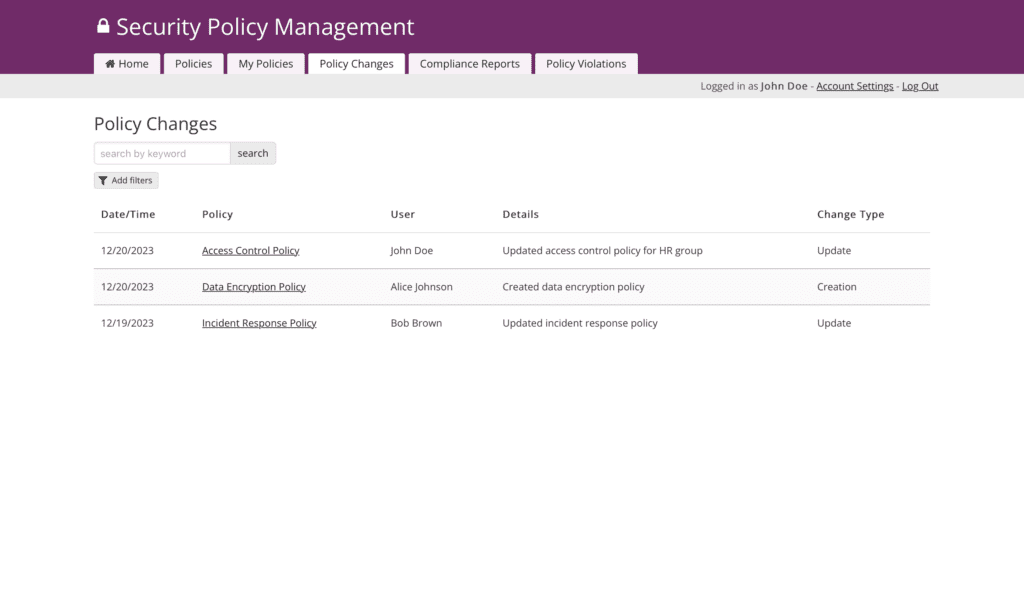
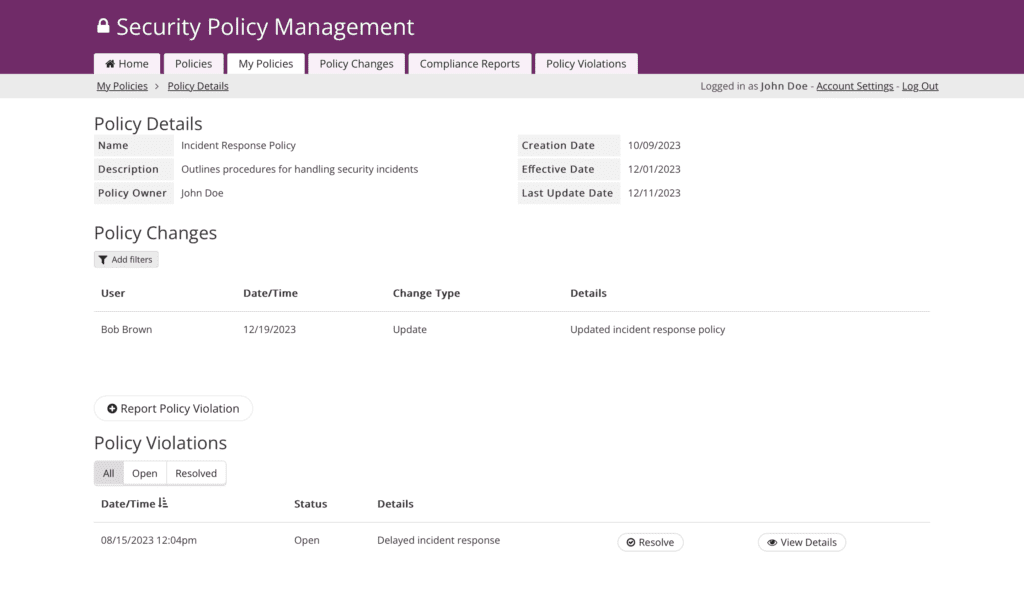
Screenshots
Why Use This Free Template?
- Track Costs Seamlessly: Managing project budgets and expenses is crucial for profitability. Knack’s app provides features for tracking project costs, managing budgets, and generating financial reports, ensuring that projects stay within financial constraints.
- Get Improve Reporting and Dashboards: This template app empowers users with robust reporting capabilities and real-time data access. It lets you generate detailed reports on project progress, costs, timelines, and other vital metrics. Access to up-to-the-minute data enables quick decision-making, helping you respond promptly to any issues or changes in the construction project, ultimately contributing to its success.
- Collaborate in Real Time: Multiple team members can collaborate on the project plan simultaneously, with changes and updates reflected in real-time, promoting effective teamwork.
- Improve Customer Communication: Utilize the template app to maintain open and transparent customer communication. Provide them with real-time updates on progress, project schedule, end dates, pricing, subcontractors, and any changes. Transparency can help build trust and keep customers informed and satisfied throughout the construction process.
- Leverage Integrations to Reach Closeouts Faster: Seamlessly integrate with other essential project management tools and software your team relies on for enhanced project management and efficiency through workflows.
Key Features
- Automated Lifecycle Management for Data Protection and Disaster Recovery Policies:
- Implement a robust automated lifecycle management system for data protection and disaster recovery policies, encompassing creation, review, approval, and publishing.
- Streamline the entire process, minimizing manual intervention and ensuring that IT security policies related to information systems and network security are consistently up-to-date.
- Granular Control over Information Technology Settings:
- Empower IT administrators with granular control over information systems and security program settings.
- Define and customize security initiatives and parameters to align with specific organizational needs and compliance standards.
- Real-time Alerts for Policy Violations and Network Security Breaches:
- Establish a real-time alert system for policy violations and network security breaches.Enable security officers and compliance officers to promptly identify, address, and rectify policy breaches and network security issues, thereby enhancing overall data protection and disaster recovery efforts.
- Role-Based Access Control (RBAC):
- Implement Role-Based Access Control to ensure that users, including employees, have access only to policies relevant to their roles.
- Enhance data security by restricting access to sensitive information based on end user roles within the organization.
What’s Next?
- Get help building your app: Request a demo
- See how this app is built: Install the Security Policy Management Template